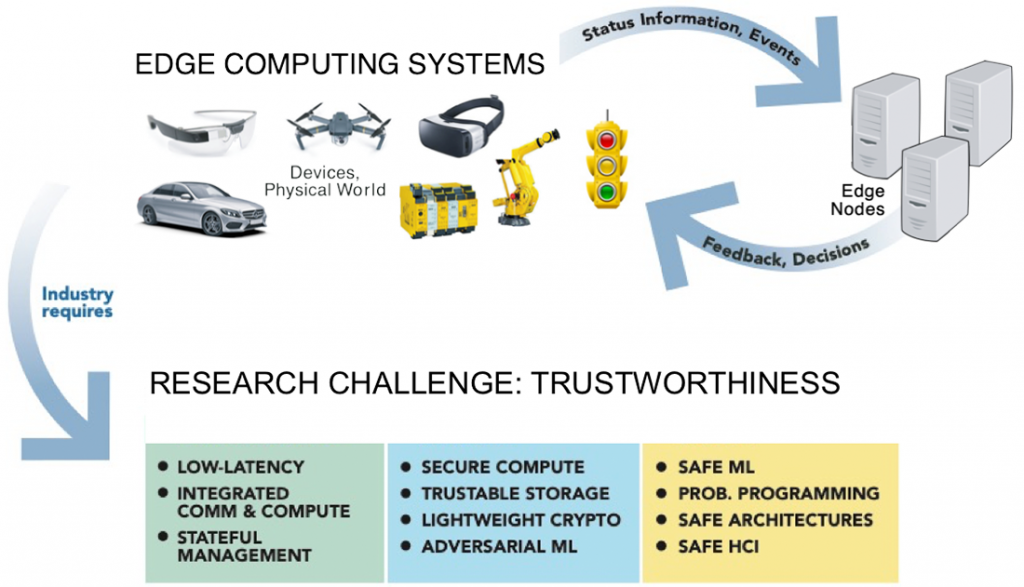
Edge systems need to be trustworthy, that is ideally always provide the correct functionality in the respective uncertain context. Trustworthiness itself requires predictability, safety and security.

The applications of edge computing are strongly relevant for a number of industrial domains, like civil security, defense, manufacturing, medtech, telecommunication and transportation. If edge computing systems and applications could be leveraged in such industrial domains, that would pave the way to significant value-adds for Swedish industries.
However, doing so turns out to be quite challenging. Large-scale industrial exploitation typically implies that the corresponding applications are mission-critical, for instance with respect to revenues, and/or safety-critical with respect to processed goods or human health. Therefore, corresponding edge systems need to be trustworthy and ideally always provide the correct functionality in the respective uncertain context – i.e. safe provisioning of instructions to humans, correct prediction of system evolution, timely coordination of CPS, etc.
Challenges
From a fundamental research perspective the following challenges arise:
Safe machine learning
Many envisioned applications for edge computing environments will leverage supervised machine learning or reinforcement learning. Edge computing is quite suitable for such algorithms, as it can provide enough compute and storage capacity, while keeping the costs for the provisioning of these capacities low. However, today machine learning algorithms come without any performance guarantees, i.e. cannot be used directly for mission- and/or safety-critical applications. Even worse, they are susceptible to adversarial attacks even if their learned data structures are not exposed. Hence, the scalable and trustworthy application of such algorithms in the context of edge computing calls for novel ways to make machine learning safe and robust.
Safety at design- and run-time
Existing safety approaches are not applicable to the contexts of edge computing systems, as traditionally safety systems are designed for well defined, and in particular confined physical environments, like caged areas in manufacturing. However, for more dynamic or even unknown environments, established safety engineering approaches fall short. In such environments, worst-case design-time safety analysis yields overly conservative results. Instead, new, quantitative and certifiable notions of safety have to be defined and safety has to be addressed both at design- and run-time.
Secure links, processing and storage capabilities
Due to the tight integration between the cyber domain and the physical world, edge computing systems and applications need to predictably and securely provide low-latency communication and compute services – data integrity and confidentiality are of essence here. However, providing these features is challenging due to the heterogeneity and distributed nature of edge computing. Wireless communication requires new approaches to realize low-latency, reliable and secure links. Likewise, due to the distributed nature edge computing comes with new attack surfaces, requiring secure processing and trustable storage capabilities.
Scalability
Traditionally, trustworthiness of critical systems has been achieved by worst-case design on dedicated resources, for instance for embedded systems. Nevertheless, in edge computing this approach is not sustainable as it does not scale, i.e. one cannot provide for each individual application a dedicated and closed edge computing system. Edge infrastructures will have to be shared, and they will have to be open while still being trustworthy. Only such an approach warrants scalability for the majority of applications. However, these requirements aggravate the above raised issues with respect to safety, security and predictability.